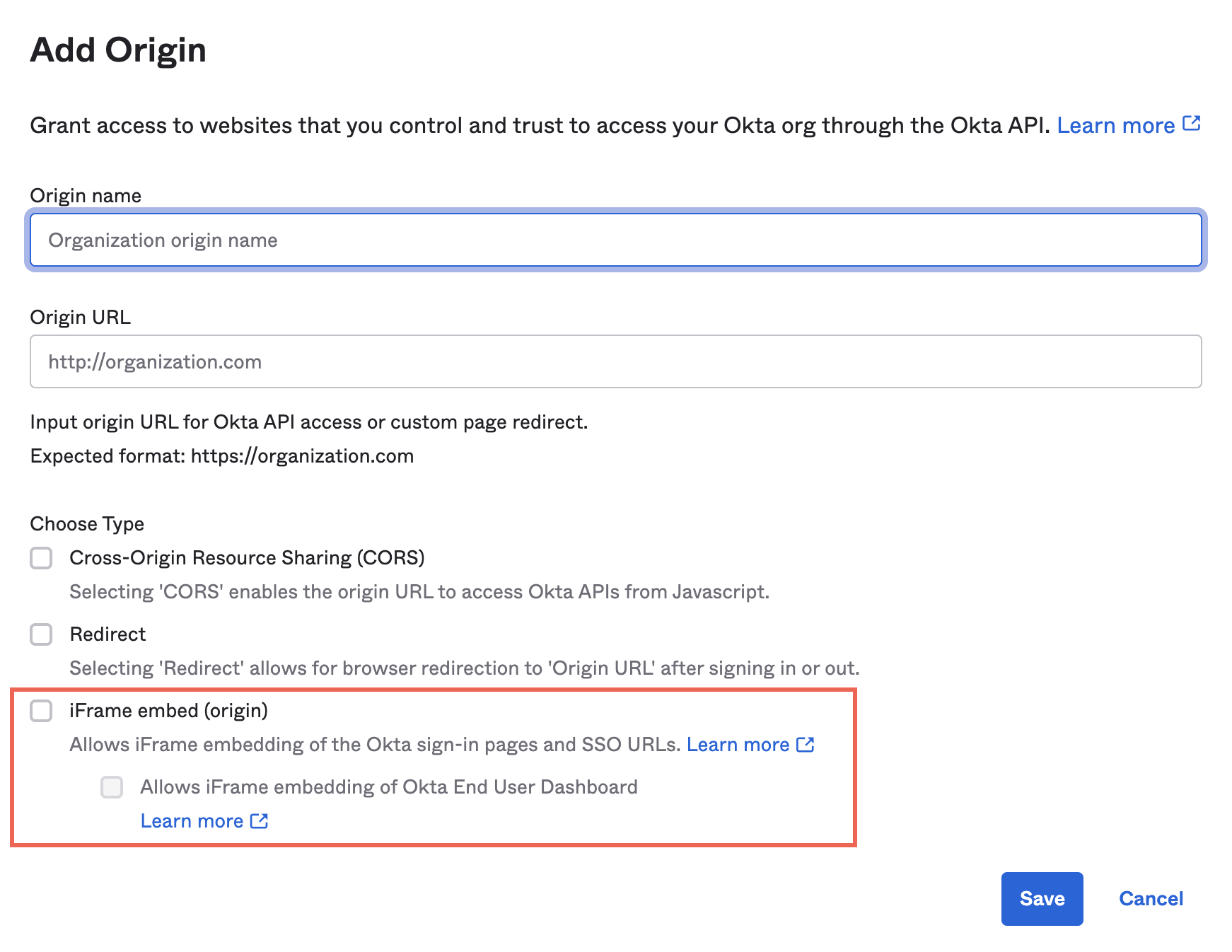
which of the following categories require a privileged access agreement
30 2020 GLOBE NEWSWIRE Simplicity Esports and Gaming Company OTCQBWINR OTCQBWINRD Simplicity Esports announced today that it signed a 30 month long sponsorship agreement with Redragon a global manufacturer and distributor of headsets. You can also reduce the time you spend on administrative tasks related to training submissions to spend more time on value-added tasks.

Powerful Privileged Access Management Cloud Or On Premises
Which of the following certifications would satisfy IAM level II and IAM level III.
. IA Technical requires a privileged level access agreement. Which of the following categories require a privileged-level access agreement. Malware that essentially is a form of social engineering because it entices the user to install the supposedly benign software.
If methods other than using privileged access will accomplish an action those other methods must be used unless. This answer was confirmed as correct and useful. Both IA Management CNDSP c.
Privileged access enables an individual to take actions that may affect computing systems network communication or the accounts files data or processes of other users. Categories and specialties within the cyberse-curity workforce that require a PAA include. In accordance with AR 25-2 whose responsibility is it to ensure all users receive initial and annual IA awareness training.
Which of the following Categories Require a Privileged Access Agreement. There can be a privileged-level access agreement for almost any sort of computer system contract document or software application. IA Technical requires a privileged-level access agreement.
This answer was confirmed as correct and useful. Worms and Trojan horses are types. Which of the following Categories Require a Privileged-Level Access Agreement.
Which if the following categories requires a privileged level access agreement. Understanding Privileged Access Management Pam Strongdm Security Tab Understanding Privileged Access Management Pam Strongdm What S New Cyberark Docs. To know who has access to these accounts you must enter all relevant applications on the network and then identify the privileged access service or proxy accounts that use these applications.
If the following categories require a preferred level access agreement. IA Technical requires a privileged access agreement. Both IA Management CNDSP c.
Therefore the idea of specific categories doesnt really apply here. If you own a training company youre probably always looking for new ways to increase the number of participants. Which of the following categories require a privileged access agreement.
Which of the following categories require a privileged-level access agreement. Privileged access may be used only to perform assigned job duties. Get 60 minutes online personalized tutoring session for each theme of all university tutor notes.
What is the purpose of a privileged access policy. Individuals seeking privileged access must complete and sign a PAA. However the best approach for each organization is.
Privileged access shall be granted to individuals only after they have read and signed this Agreement. IA Technical require a privileged-level access agreement. AGREEMENT Privileged Access is the authorized access that provides a capability to alter the properties behavior or control of the information system or network.
Both ia management cndsp. Which of the following categories requires a privileged access agreement. You can enable Audit Directory Service Access Group Policy to monitor the.
Privileged access is granted only to authorized individuals. Many organizations have a similar path to maturity eligibility prioritizing first simple profits and the greatest risks and then gradually improving preferred security controls across the enterprise. Both ia technical ia management.
Worms and Trojan horses are types. Your data including personal data is safe with us. Individuals with privileged access must respect the rights of system users respect the integrity of systems and associated physical resources and comply with all relevant laws or.
Any time private information is shared a master user must decide which other users may be privy to the information and how. Why can melted paraffin drop a certain height and not just rub on the skin. This answer has been confirmed as correct and helpful.
Both IA Technical IA Management b. All this extra privilege adds to an inflated attack surface. Privileged access enables an individual to take actions which may affect computing systems network communication or the accounts files.
1 Those requiring modification. Which of the following categories require a privileged access agreement. Boca Raton Florida Nov.
Routine computing for employees on personal PC users can include browsing the web streaming videos using MS Office and other basic applications including SaaS for example.

App Consent Grant Investigation Microsoft Docs

Automatically Apply A Retention Label Microsoft Purview Compliance Microsoft Docs
Understanding Privileged Access Management Pam Strongdm

Controlling Access One Element Of Cybersecurity Article The United States Army

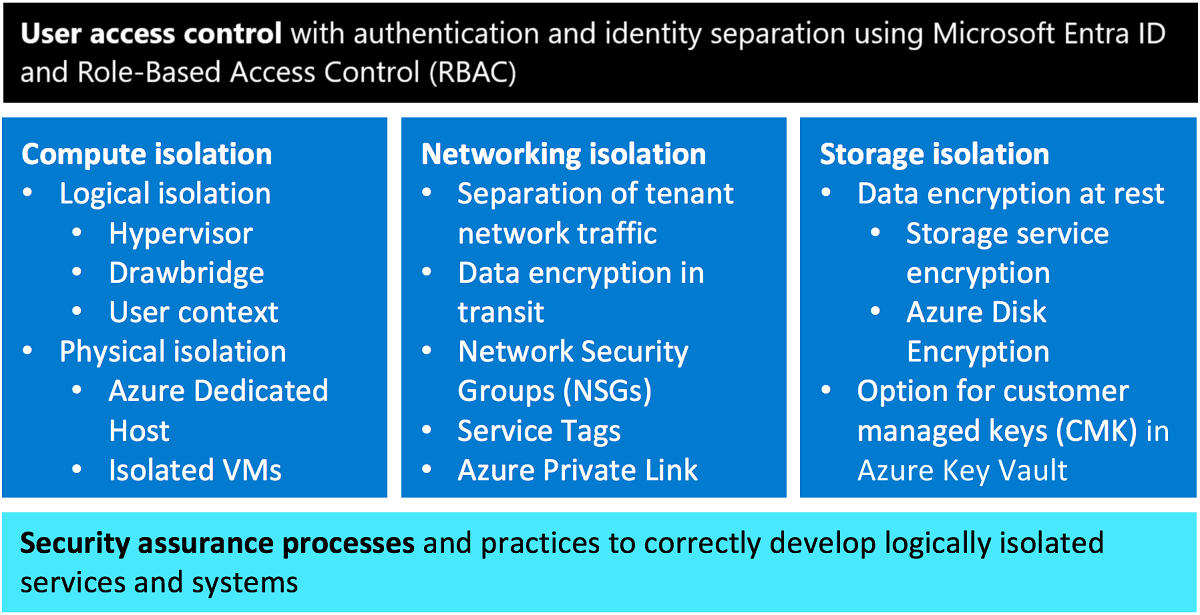
Azure Guidance For Secure Isolation Azure Government Microsoft Docs
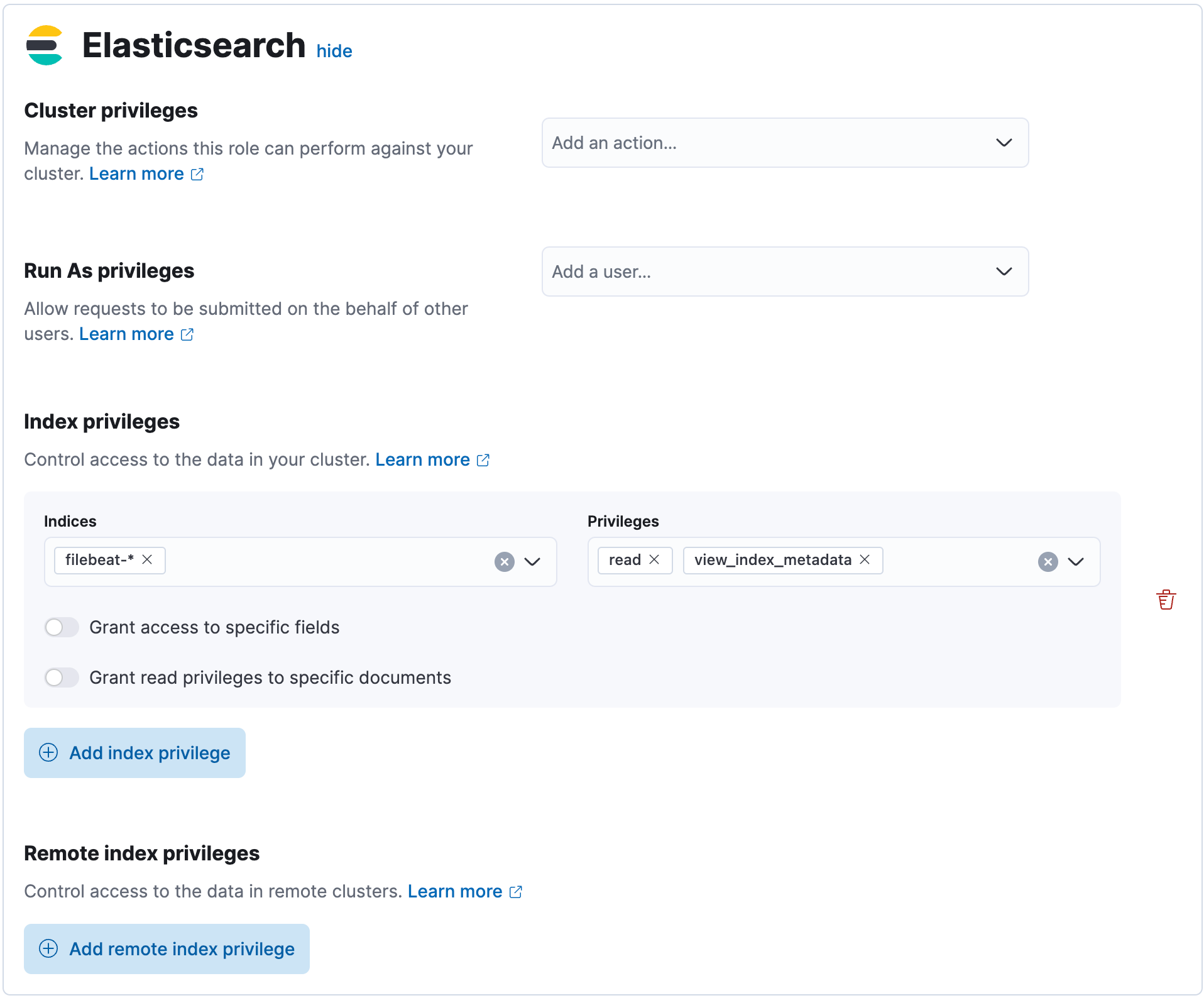
Kibana Role Management Kibana Guide 8 3 Elastic
Knowledge Base Article Service Portal
Securelink Enterprise Access Third Party Remote Access

What Is Privileged Access Management Pam Explained Security Wiki

Understanding Privileged Access Management Pam Strongdm

Understanding Privileged Access Management Pam Strongdm
What Are The Different Types Of Penetration Testing Purplesec

How To Detect And Prevent Industrial Espionage With Examples Ekran System
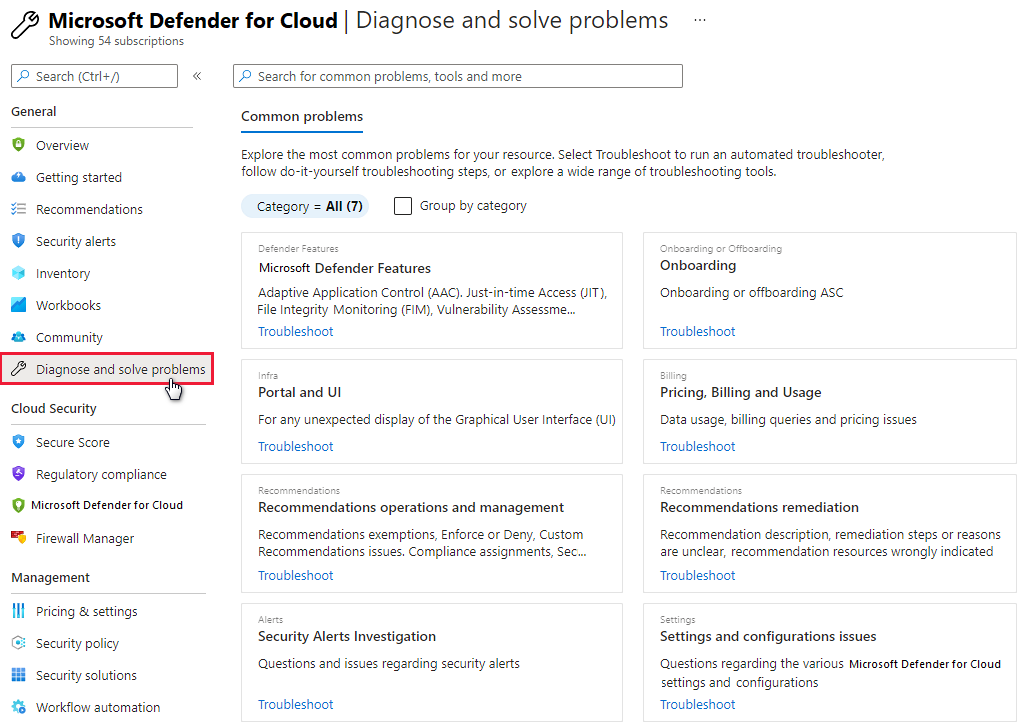
Archive Of What S New In Microsoft Defender For Cloud Microsoft Docs

Understanding Privileged Access Management Pam Strongdm
What Is Privileged Access Management Pam Explained Security Wiki